Title
Create new category
Edit page index title
Edit category
Edit link
Overview
Welcome to the developer documentation for our AI Services for Terminals. This documentation is targeted towards integrations relating to Non-browser based clients and ePOS terminals. It includes the following:
- Age estimation
- Anti-spoofing
- Face capture
You will need to create a Yoti Hub account with an e-mail & password or using the Yoti App on your phone and register your business with Yoti. Click below for more info.
Technical overview
The user's image is securely transmitted to the Yoti API (hosted in the United Kingdom and uses TLS 1.3 encryption in transit).
Optionally, you can use Anti-spoofing to add a layer of security to the service and ensure the user is using their own face for estimation. Yoti uses machine learning to train a deep neural network to recognise presentation attacks. This will help prevent malicious users trying to user a fake image to get a higher or lower age estimation than a legitimate attempt would produce.
After the service performs the processing, the captured facial image is discarded and Yoti API returns:
- Age check result or Predicted age with uncertainty value.
- Anti-spoofing predicted value.
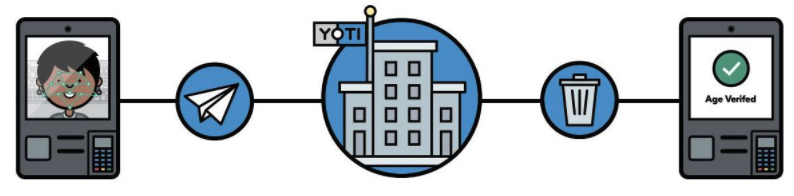
Facial age estimation overview
To read more about Age estimation and Liveness, please see our white papers.
Got a question? Contact us here.